Category
Level
Price
Language
Rating
12 Courses are found
 Beginner
Beginner
Certificate in Ethical Hacking
The Certificate in Ethical Hacking is a foundational program designed to provide learners with a comprehensive understan...
 Beginner
Beginner
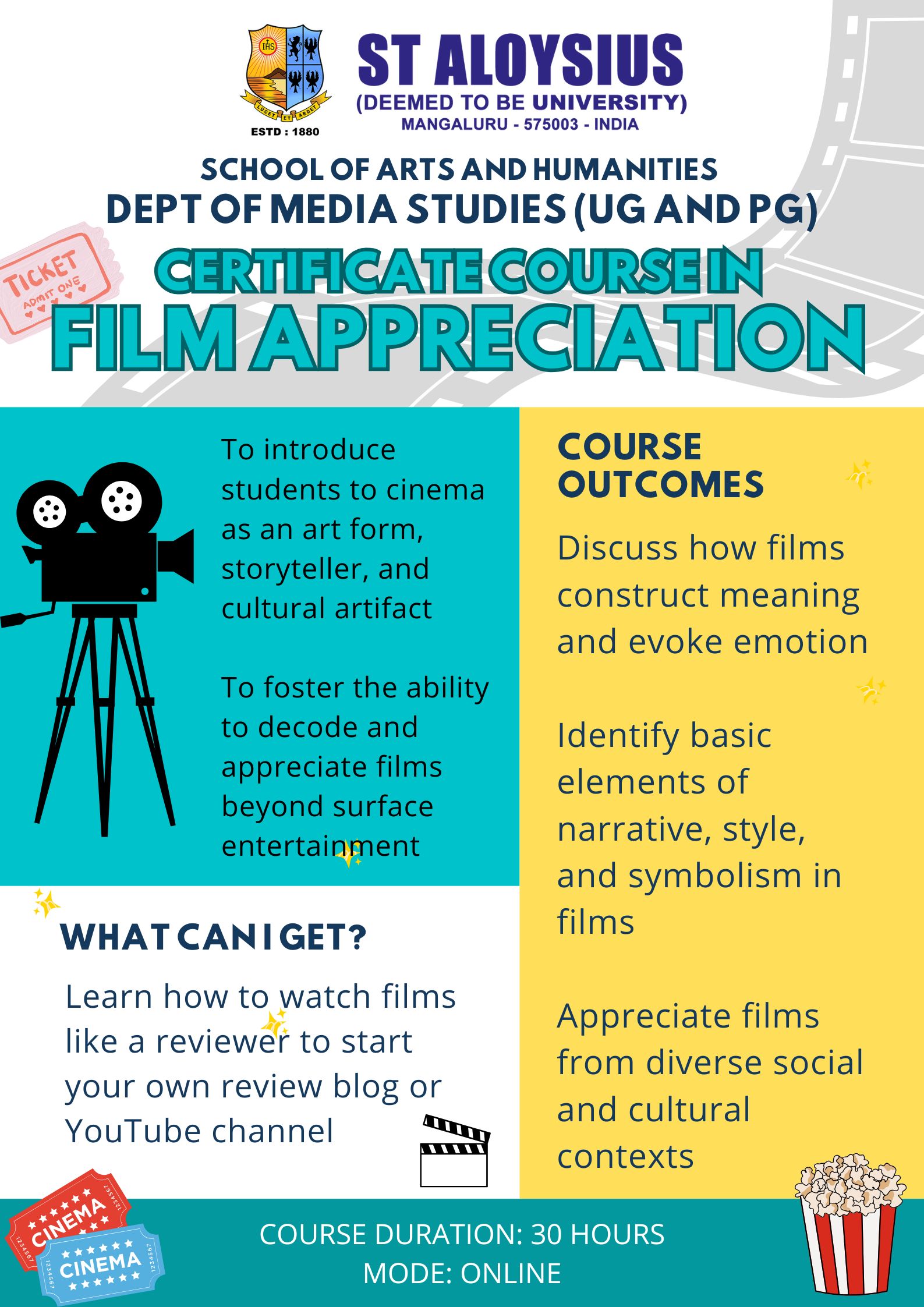
CERTIFICATE COURSE IN FILM APPRECIATION
ObjectivesTo introduce students to cinema as an art form, storyteller, and cultural artifactTo foster the ability to dec...
 Beginner
Beginner
MASTERING SOFT SKILLS
The Department of History is proud to offer an offline Certificate Course in Soft Skills, designed to equip learners wit...
 Beginner
Beginner
Gym Trainer/Instructor
This course provides a comprehensive introduction to the principles and practices of gym training through a balanced com...
 Intermediate
Intermediate
Essential for Life Skills Education
Course overviewEssential Life skill education is a unique and effective programme which enablesindividuals to adopt and...
 Beginner
Beginner
Visual AI Content Generation
Visual AI Content Generation is a beginner-friendly certificate course that focuses on how to thoughtfully use AI as a c...
 Beginner
Beginner
WORKPLACE CIVILITY AND INTELLIGENCE
This certificate course is designed to help students develop the social, emotional, and professional skills required to...
 Beginner
Beginner
INTERNATIONAL BUSINESS
This course, " INTERNATIONAL BUSINESS," offers students a comprehensive exploration of economic diplomacy. Over 30 hours...
 Beginner
Beginner
New Product Development in the Food Industry: From Concept to Commercialization (with Entrepreneurship & Startup Essentials
The Certificate Course on New Product Development in the Food Industry: From Concept to Commercialization (with Entrepre...
 Beginner
Beginner
Hindi Tranlsation
Course Code : LC7GUCE140 aहिंदी विभाग, संत. अलोशियस (मानित विश्वविद्यालय) मंगळूरु, हिंदी में अनुवाद सर्टिफ़िकेट कोर्स(Ce...
 Beginner
Beginner
Better English for Effective Communication
MODULE I: BETTER PRONUNCIATION (15 Hours)1. Introduction to 44 sounds of English through IPA script (3 hrs) 2. Word acc...

